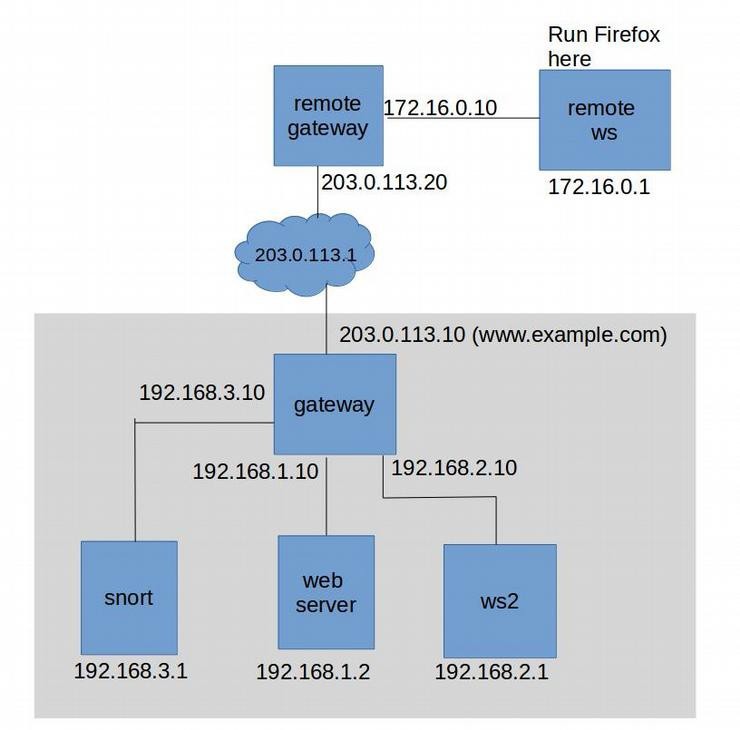
Overview
The lab’s goal was to practice network reconnaissance and basic security analysis under Linux.
Students used Nmap to scan the network, identify open ports, analyze ICMP/TCP responses, and detect active services on the FriedShrimp machine.
Once the IP address and SSH port were identified, a secure SSH session was established to retrieve a protected file.
The exercise also included SSH hardening and Bash scripting for automation and reproducibility.
🛠️ Technologies / Tools
- Nmap — Network scanning and port discovery
- SSH (Secure Shell) — Secure remote connection
- Linux CLI / Bash — Command-line operations and task automation
🎯 Key Learnings
- Understanding of network discovery and ICMP/TCP response analysis
- Securing remote access using SSH
- Automation with Bash for reproducible Linux security workflows